Performance evaluation and Comparative Analysis of Digital forensic tools in Android mobile Devices
Chapter One: Introduction
The project is divided into various chapters and sub-phases each with a distinct header illustrating the topic. The rest of the chapters are highlighted and organized as follows;
Chapter Two: Literature Review
2.1. Introduction
The aim of this chapter is to review literature related to the research field. This chapter is divided into various sections, related to digital forensic as subject field, mobile forensics, and android forensics, anti-forensics and performance evaluation of forensic tools.
The first section provides a general background knowledge to the field of digital forensics as a whole. In this section, the definition of digital forensics is outlined. This section states the difference between computer forensic and digital forensics, and outline the different fields that form digital forensics. The second part gives a detailed literature into mobile forensics and the persistent challenges facing investigators in the field of mobile forensics.
The second section gives a detailed review of mobile investigation process. This sections outlines the various principles and steps taken in carrying mobile related forensic investigation. In this section, a detailed explanation of the various steps are given. This section also highlights the field of digital forensics and smartphone devices.
The third section is dedicated to field of android operating system and android forensics. The first part of this section gives a short review into the different types of android forensic tools and highlights the specified tools to be used in this thesis. The second section gives a detailed review on the android operating system, the structure and what they entail. The second part of this section gives a review of literature on android forensics. In this section, the various methods of extraction were outlined. The third section gives a review of past works done in the field of android forensics.
The fourth sections is related to the field of anti-forensics. The first part gives a detailed definition and outlines the threat of anti-forensics in the digital community. The second part of this sections discusses the various methods and techniques involved in carrying out anti-forensics. The second part gives a review on the anti-forensic side of android operating system and review part works done in the field android in respect to android.
The fifth section gives a review of literature on performance evaluation of mobile forensic tools. In this section, a review of literature was done on past works in respect to performance evaluation. This section reviews technique and looks at techniques taken in reviewing performance of android forensic tools.
2.2. Concepts of Digital Forensics
The term digital forensics (DF) as defined by the Digital forensics Research Workshop in 2001 (Carrier, 2003) as:
“The use of scientifically derived and proven methods towards the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations.”
It is a branch of forensic science which focuses on the recovery, examination and investigation of evidence stored or hidden on computers and various other digital devices (Harrington & Michael, 2015). Digital forensics possess a big difference from computer forensics as DF not only deals with evidence gotten from a computer, but with evidence gotten from any digital devices which stores data in binary formats or electronic forms.
This can be described as the process in which electronic or digital evidence is handled from the point in which is preserved, to the point where the evidence gotten is presented and used to in a legal situation. The concept of digital forensics is used in the presence of electronic related crimes that are perpetrated with the use of electronic or digital devices such as computers, smartphones, and tablets. An example of such case is the use of computers in carrying out fraud like activities in banks and also a situation whereby a suspect stores incriminating files such as child pornography on an electronic device. The concept of digital forensic plays an integral role whereby an investigator must apply this concept in carrying out such investigation in a forensically sound manner and the environment without the alteration and loss of the digital evidence. A digital evidence is classified as evidence that are in digital format or binary formats that are used to support or refute a crime during a digital investigation. The essence of digital evidence plays a vital role in the process of an investigation and also aids the reconstruction of an event for further analysis (Carrier, 2003).
Digital forensic can be classified into several fields such as mobile forensics, network forensics. The figure below presents the different fields in digital forensics. These include network forensics, database forensics, forensic data analysis, computer forensics and mobile device forensics. For this research thesis, emphasis will be placed on the mobile forensic field.
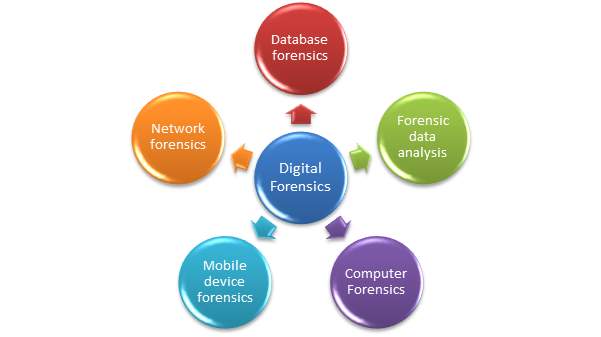
Figure: types of digital forensics(niitconsulting, n.d.)
2.3. Mobile Forensics
Mobile forensics is the branch of digital forensics which relates to mobile devices and how digital evidence can be acquired and extracted from these devices in a forensically sound manner. Various research works have been carried out in the field of mobile forensics and work research work are still ongoing due to the dynamic nature and rapid development in the field of mobile devices.Namrata R, et al (2013) posits that need for the branch mobile forensics arises due to the increase in the rate at which mobile related crimes are committed anually. Due to the increase in the use of mobile devices globally for transactions and also the flexibility of these devices, criminals have opted for the use of mobile devices in carrying out crimes due to the nature of these devices and the easiness of movement when using these devices. This is also stated by (Rizwan & Rajiv V., 2008) that the need for mobile forensics is to help in the investigation of mobile related incidence due to the ever growing use of mobile devices by organised crime syndicates to evade law enforcement officers.
2.3.1. Challenges Faced by Investigators in Mobile Forensics
In carrying out an investigation involving mobile devices, investigators and examiners are faced with various daunting difficulty and challenges. In defining these challenges, these issues are categorized into two main classes of challenges namely; the Technical challenges and the legal challenges.
2.3.1.1. Legal Challenges
The ever growing issues of privacy. The issue of privacy is another major issue that an investigator encounters with when dealing with a digital investigation. According to (Jason, et al., 2011) investigators must deal with laid down privacy laws when carrying out an investigation. There must be proper acquisition and extraction of the specified and exact digital evidence from a mobile device. In the process of collection of crucial evidence, an investigator must not in any situation try and extract or alter the evidence that is irrelevant for analysis in a digital investigation. The privacy issue is one in which investigators will tend to contend with even in the nearest future such as European laws on privacy and data protection that regards personal data as private and sensitive.
The issue of integrity and reliability. (Jason, et al., 2011) Stated that the issue of integrity and reliability of digital evidence from mobile devices is one in which both investigators and courts face. This is due to the ever changing nature and diversity of mobile devices. Evidence gotten from mobile devices will constantly be under scrutiny. Also due to the unstable nature of most mobile devices, evidence can be altered when carrying out an investigation. Forensic techniques and methodologies can cause a change in evidence output. Taken into consideration that most forensic tools do not provide proper or full forensic imaging of a mobile device thereby creating room for integrity issues.
The issue of collection and preservation of mobile devices and digital evidence. The method of collection and preservation plays an important significance in the process of mobile investigation. This plays a crucial part as investigators must contend with the issue of carrying out a forensically sound extraction and acquisition of evidence from a mobile device in other not to alter evidence. Also, during this process an investigator must be able to make sure all evidence has been collected properly and not missed or omitted. A typical example of such is when carrying out cell phone forensics on a suspected criminal. An investigator must make sure when preserving evidence such as a voicemail, proper preservation and collection must be done on such vital evidence or this can become a problem during presentation in a court case as the authenticity of such evidence can be disputed by another suspect or party.
2.3.1.2. Technical Challenges
One of the major technical challenge and difficulty of carrying out a mobile forensics investigation is the ever-growing number of mobile devices in the market. Many researchers have argued and pointed out the ubiquitous nature and growth the number of mobile devices poses a great challenge to an investigator, this is due to the fact that an investigator must keep a constant tab on almost all mobile devices out there in use. Due to the rapid growth in technological advancements and the increase in the popularity of mobile devices, this poses a great challenge for investigators and law enforcement officials globally. (Agrawal, et al., 2013) posits that due to the ever increasing growth of the mobile device market, there will also be an increase in their use for criminal activity.
The diversity of Operating Systems and Manufacturers. One major issue in which investigators and researchers face in terms of mobile forensics is the problem of multiple operating systems running on mobile devices meant for investigation. According to Oleg Davydov (eforensics magazine, 2012) posits that due to the high number of operating systems in the market today, examiners much first take the tedious tasks of getting to know what operating system is running on the mobile device before carrying out any process of extraction or acquisition and also not to tamper with the evidence on the mobile device. This can be attributed to the fact that despite most OS approximately offer almost the same functions and options, they differ greatly in the way data is handled and stored, access policies, security functions and overall characteristics. There are multiple varieties of operating systems with different filesystems Such examples are the android operating system and the IOS operating system. The different nature of the OS poses many technical issues as these OS tend to store data In different layer. An android operating system for example, tend to be different in different phone manufacturers. Manufacturers tend to customize the way the andriod OS stores and and protect files.
Another challenge faced by an investigator in carrying out mobile forensics is the type and nature of the data storage and device architecture. This issue is due to fact that mobile device makes use of volatile memory in which they store data and information. Mobile devices makes use of the Solid state hard drives (SSD). The use of SSD by mobile device poses a great challenge due to the nature in which they work and perform. According to Sheward (2012) SSD poses a great challenge because they operate differently than the conventional magnetic hard drives found on computers. Most Solid state drives run on different file system architecture. An example is Yet Aother Flash File System 2 (YAFFS2), due to the nature of these systems running on flash memory. Investigators have to contend with the issue of extracting artefacts from thes type of structure. Commercial Forensic tools tend to fault or fail to detect these type of memory structure. An investigator must first contend with getting a specialized tools in extracting this system, and contend with the problem of alteration.
The problem of power and data connection issues. This one of the prevailing challenge in which an inveestigator faces when handling and carrying out a forensic investigation on a mobile device. Due to the volatile nature in which data is stored on mobile devices, investigators must contend with the power preservation of the mobile device or risk losing critical digital evidence when power is lost. A complete loss of power in the mobile device equates to a complete loss of information (Kyle D & Richard P, 2008). Also, the issue of data connectors for mobile devices poses a challenge. Many devices such as GPS, smartphones and Tablets makes use of variety of cables to connect, charge and extract information from them. An example is an iphone cable connector which differs from a standard blackberry cable, this gives an examiner the problem of keeping tabs with what cable to use and also the issue of mobility of those cable to the crime scene.
No standard or De-facto methodology for carrying out mobile forensics. The rapid growth in the number of mobile devices and also the ever changing nature of Operating systems and hardware presents a very daunting challenge to investigator in terms of the methodoly to be used in carrying out an investigation. Many researchers and forensic bodies have come up with different methodologies for carrying out different investigations on different mobile devices. This creates a very huge task for the investigator to master or come up with a unique methodolgy when performing mobile forensics.
The data acquisition and preservation challenge. The acquisition and preservation of digital evidence have been one of the most persistent challenges of mobile forensics. This is due to the sensitive and fragile nature of mobile devices. Investigators face a great challenge in the acquisition of critical evidence from a mobile device due to the procedures and techniques in which a forensically sound process must take place. In a conventional scenario involving a computer system, an investigator can carry out either a dead or live acquisition or analysis of the computer such as getting the image of the victim’s system. However, the case and scenario is quite different when carrying out a mobile forensic investigation, and an investigator must consider the state of the device if it is switched off or switched on. This is due to the fact that switching off such device can tamper with the evidence and reduce the integrity of the evidence on the device, and also if the device is switched off an investigator must consider not switching on the mobile device in order not to activate encryption mechanism or allow a remote wipe of the mobile device from a remote location.
The problem of selecting a tool. Investigators face a huge challenge is selecting a specific tool as some mobile forensics tool can tend to omit some evidence while another can find this evidence. Most forensics tools do not support some mobile devices thereby making in very difficult for carrying out an investigation. Example of such tools are standard forensic suites are computer based versions like Encase. The lack of evaluation of some forensic tools, an examiner is faced with the problem of selecting the right tool for a forensic investigation. The lack of a standardized evaluation of tools creates a daunting task for the investigator.
Another major challenge faced by investigators is the issue of anti-forensics. Anti-forensics practices and techniques are currently evolving and spreading, proving a great issue for many investigators to challenge with the growth in the use of these techniques by many criminals to countermeasure investigative processes in an investigation. According to (Mubarak & Ali, 2013), attackers deliberately make use of anti-forensic tools to mask or hide critical digital evidence. This will be discussed in further in this section of this thesis.
Another major challenge faced by investigators in terms of mobile investigation is the integration of most mobile devices with cloud computing services. According to (Vohra & Varun, 2014) the incorporation of mobile devices with cloud services in other to reduce the computational power and energy consumption of the device’s battery, will cause a very great challenge to investigators in the present and future. This is due to the fact most work will be done remotely on a server with an unknown location. This poses a real threat in the process of a digital investigation as potential digital evidence can be difficult to extract from the mobile device and also the problem of location.
2.4. Mobile Forensic Investigation Process
In carrying out a digital investigation, there are various investigative process method which must be followed. Various bodies and examiners have over the years come up with various methodology and procedural approach for both computer based and mobile based investigation. The Association of Chief Police officers (ACPO) laid down four major principles and guidelines to consider when carrying out computer related investigations. This can be found in the appendice section.
2.4.1. Identification and Preparation
In the process of a mobile investigation, an examiner must be required to first carry out the process of identification and preparation. In this phase, (Murphy, 2013) states that an examiner must be able to identify the following details. These are;
The need for identification by an examiner creates a preperequiste to the other phase of the investigation. This creates an avenue for a more secured and procedural way of carring out an investigation, thereby reducing the risk of loosing vital evidence and minimising the challenges ahead. An examiner must be able to identify critical evidence and also able to identify what make, model and type of mobile device is used.
In the preparation phase, an examiner must carry out an extensive research into the mobile device been investigated. This gives the examiner more detailed knowledge into what type of architecture is running on the device, the nature of the filesystem and also what type of tools to use for the cause of the investigation. Using previously identified details in the identification phase, the examiner must specify what appropriate tool is needed and what type of evidence must be extracted from the mobile device in question (Murphy, 2013). Also, an examiner must be able to identify specific type of forensic tools used for a particular mobile device. This creates a situation of the next stage of mobile forensic process model. The wrongful selection of forensic tools leads to either loss of integrity or non retrieval of vital digital evidence.
2.4.2. Preservation
The concept of preservation of digital evidence plays a crucial role in a digital investigation. Preservation of digital evidence deals with the process of preserving the integrity of a digital evidence in a forensically sound manner. Preservation of mobile device data presents lots of unique challenges. Several mobile devices may require special cable types and may require additional equipment in other for the device to connect to the digital forensic workstation. (Ahmed, et al., 2014). This involves taking procedial steps in preserving evidence integrity such as isolating the mobile device, securing relevant log files, and collecting volatile data that would be lost when the mobile device is powered off (Casey & Schatz, 2011). Isolation of mobile device also place a crucial part in preservation. When carrying out preservation of data, an examiner must carefully choose the tools used for preserving mobile devices (Lesemann & Mahalik, 2008). The essence of selecting the right forensic tools for preservation is critical due to the fact most forensic software applications sometimes might not have the necessary drivers installed to establish communications with the mobile device (Ahmed, et al., 2014). In other to preserve vital evidence, most forensic tools introduce special software into the mobile devices in other to preserve the evidence, but from a legal and forensic point of view this creates a problem of intregity as the introduction of these software’s into the device creates an avenue for alteration of the mobile device evidence and in some cases overwrite the evidence. In order to uphold the intregity of mobile forensic evidence, the need for cryptogragphic hash signatures of evidence must be the taken to ensure that evidence acquired from the mobile device has not been altered by the software agent (Ahmed, et al., 2014).
2.4.3. Acquisition and Verification
Acquisition can be described as the process of imaging or otherwise the process of obtaining information from a digital device (Raghav & Saxena, 2011). This deals with the process of extracting evidence from a mobile device. As one of the major criteria of a digital investigation, the process of data acquisition can be very challenging.Highligthed as one of the major challenges faced by investigators, the concept of acquisition plays a major role. Due to this, many researchers and authors have proposed various methods of acquisition of data. These method are; manual extraction, logical extraction, physical extraction, JTAG acquisiton and chip-off acqusition (Alghafli, et al., 2012). The use of these acquisition methods varies and depend on the type, state and the nature of the mobile device. In carrying out acquisition, an examiner must be able to collect evidence based on forensically sound principles.
2.4.4. Examination and Analysis
Examination can be described as the process of looking for potential hidden storage locations of data such as unallocated space and slack spaces (Johnson, 2014). This stage involves the examination and analysis of extracted evidence. This process involves filtering, searching and evaluating retrieved data. Analysis involves the scrutinizing of digital evidence to find relevant data that are necessary for a forensic investigation.
2.4.5. Documentation and Reporting
This is the final stage of any digital forensic investigation. This involves the presentation of analysed and examined evidence in a presentable format. This stage requires evidence be presented in a readable and presentable format to a court of law.
2.5. Android Forensics
According to Ayers, et al.(2005) there are many variety of forensic software’s for carrying out mobile device forensic investigation. As stated by the author, an ample number of forensic toolkits and software tools exists, but the range of devices they support differ and are narrowed down to distinct platforms for a manufacturer’s product line, the hardware architecture or the family of operating systems (Ayers, et al., 2005).
Forensic tools can be classified into two major categories namely software based tools and hardware based tools. In terms of android, there exist many tools which support extraction. But according to Liu, et al (2011) most forensic tools available today presents a problem of reliability, effectiveness and validity when carrying out forensic investigation. For this thesis, focus will be placed on extraction based forensic software’s. Android forensic tools consist of both commercial and open-source tools. Due to time constraint, cost and availability some commercial forensic software, the use of their commercial lite versions will be employed.
2.5.1. Android Operating System
Android operating system is an open source mobile device platform based on the Linux 2.6 kernel and later. Android was developed and is managed by the Open handset Alliance (OHA), a group of carriers, mobile device and software vendors, and component manufacturers (Hoog, 2011). According to Mohindra (2008), the main motive for the development of Android operating system was to facilitate openness in mobile software. Android was built to enable developers to create compelling mobile applications that take full advantage of all a mobile device has to offer. Android applications are written in JAVA and interacts with the Android framework layer through well defined Application programming interface (API). Android makes use of JAVA programming language, which is widespread and the Dalvik Virtual Machine. It is divided into four layers, including five different group. Android operating system uses the sandbox concept, where applications have their their reserved areas, with isolated running environments and limited acesss to resources (Morun de L Simao, et al., 2011). Android relies on a permission-based system with a sandoxing structure to enforce security (Do, et al., 2015). Upon installation of any application, permissions are granted to applications based on the permission defined in the “AndroidManifest.xml” file.
Android Architecture
According to Ahmed, et al.(2013) , android consists of a stack of software components which are divieded into five major compnents. The figure below gives a detailed image of android architecture.
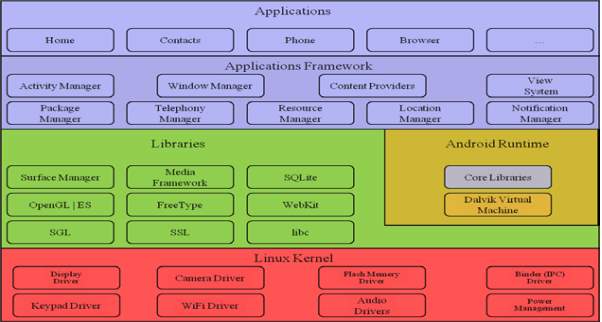
Figure: Android Architecture
According to (Ahmed, et al., 2013) the application layer consists of set of typical applications for mobile devices (e.g. text-messaging management, browser, e-mail clients, contacts management) written using the JAVA language.
The application framework provides an open and standardized development environment that allows, with the assistance of content providers and other serives, the reuse of application functios and features (Andre, et al., 2011). According to (Ahmed, et al., 2013) android frameworks provides services through a wide range of Application programming interfaces (APIs).
The android runtime consists a set of core libraries and the Dalvik Virtual machine. As stated by (Ahmed, et al., 2013) in the android run time, each running application holds its own instances and carries out execution in its own process.
The android library consist of a set libraries written in C/C++ language. As outlined by (Ahmed, et al., 2013) the android library are used by the components of the android system the application framework.
The Linux kernel is main core of an android platform. As stated by Vijayan (2012) the Linux kernel controls the hardware component and the resources of the mobile device. According to Hoog (2011) controls and maintains the drivers of hardware on the android device
2.5.2. Android Forensics and Tools
The concept of android forensic is a relatively new research area since the the lanch of the android operating system. Based on the concept of forensic which deals with the techniques and methods used for the extraction, examination and presentation of digital evidence for the process of admissibility in a legal case. Various researchers have worked on works based on the acquisition and extraction capabilities of android forensic tools. One of the main challenges facing android devices today consist of data extraction and data preservation. As such, alteration and integrity of data acquired also pose a challenge (Zlatko, 2012).
Hoog (2011) research work “Android Forensics” laid a solid foundation in the concept of android forensics. In the research work, the author gave a very detailed concept on android operating system, andriod forensic acquisiton and analysis. The author highlighted the two major methods of acquisiton namely physical acquisition and logical acquisition, and the differences between the two types of techniques. According to (Hoog, 2011) it is nearly impossible to carry out foresic analysis on an android device with any impact on the device. In the research work, emphasis was placed on the concept of installing an external exploit on the device called rooting to acquire forensic evidence from android devices. Also emphasized were the type of evidence and the procedure used in carrying out android forensics. The author proposed four different approaches in carrying out android forensics namely Chip-off, Physical acquisition, logical acquisition and SD card Analysis.The use of an open source tool called AFLogical was used in carrying out the investigation. For this thesis, the performance of this tool will be evaluated.
lessard & kessler (2010) emphasized the need of acquisition of valuable evidence from android operating system. In this research, the authors made much emphasis on the use of the Android Debug bridge (ADB) and the essense of rooting the android device into other extract valuable information. The author describe the need for the android debug bridge and it’s essentiality to the cause of an effective forensic investigation on android devices. lessard & kessler (2010) states that the use of a “dd” tool can be effective in the acquisition of android device image.
Vidas, et al. (2011) proposed a different method for the collection for android devices. In the author’s research work, a different approach was taking to acquire data through the use of special boots methods. The authors made use of custom recovery booting for the acquisition of evidence and imaging of the android device. The authors emphasized that this method provided integrity and admissibility of evidence. Due to the fact that the method avoids the possibility of alteration of evidence as opposed to that of (lessard & kessler, 2010) and (Hoog, 2011) rooting technique which makes use of an exploit. This giving room to alteration of the device and reducing the integrity of the evidence acquired.
Barghuthy & Marrington (2014) carried out a comparison of forensic acquisition techniques. In the author’s work, the rooting technique proposed by (Hoog, 2011) (lessard & kessler, 2010) and custom recovery (Vidas, et al., 2011) were compared and evaluated based on the investigation of orweb browsing sessions. (Barghuthy & Marrington, 2014) concludes that the rooting technique modifies the android’s partition while custom recovery retains integrity. But stressed that the result outcome of evidence of both techniques remain the same. This hypothesis was based and limited to the recovery of private orweb browsing sessions. In this research work, the author posits that rooting method should be used when there little or no option of other recovery methods.
Macht (2013) emphasized the essence for a live forensic framework for android mobile devices. In the author’s research emphasis were upon further work extension on the volatililty framework. In this research work, emphasis was placed on the need for acquisition of RAM artefacts in android operating system.This research focused on the development of a software stack for the volatility framework with additional and more advanced application analysis and plugins for creation processes.
Konstantia, et al (2013) gave an overview on the critical challenges of mobile device device forensic an emphasis to android device forensics. The author’s review of the state of android forensics, the challenges and also the future challenges ahead in android forensics.
Kaart & Laraghy (2014) stressed the need for the interpretation of timstamps when carrying out a digital investigation. In their research work, the authors presented a case study were time stamps play a crucial role in an investigation and stressed the need for verification and giving high details to the time zone of the android device. This helps protect the integrity of the evidence presented. Also, locations of finding the timestamps information were also given. The location stressed is /data/data/com.android.providers.settings/databases/settings.db.
Busstra, et al. (2014) proposed an approach in the extraction of android artefacts using Wi-FI. In the author’s work, emphasis was placed on the issue of connectivity by forensic softwares in extracting evidence. the author’s stressed the problem of evidence collection in the absence of a USB-connection cable or problems with the USB ports of the device. Also pointed out, that most forensic softwares do not support the use of alternative methods other than the USB connection. The authors proposed an approach in using Wi-Fi in extracting critical data. In doing this, the author’s expressed the need of the android device to be rooted. In carrying out this process, the need for access to the device is required. In the case the device is passworded or locked such approach cannot be implemented.
Martini, et al. (2015) emphasized on an in-depth analysis and evidence collection system for android devices. In their research work, a proposed conceptual model for evidence collection was developed for forensic practitioners. The methdology proposed emphasized the need for real-time incidence respnse evidence analysis for organisations.
In conclusion, various methods have been proposed by researchers in terms of android forensic acquisition and extraction. As such, researchers have argued on the integrity of various methods used. Of such, few researchers have argued on the concept of using a root exploits in respect to data integrity and data admissibilty.
2.6. Anti-forensics in Android
2.6.1. Anti-forensics
Anti-forensics (AF) is a multi-headed demon with a range of weapons in its arsenal. Major forensic programs have started to attract unwanted attention from security researchers of a type that have plagued mainstream software developers for years (Hilley, 2007).One of the major issues faced in the digital age and in carrying out an investigation is the issue of anti-forensics. Anti-forensics is one of the major problem faced by both the research communities and law enforcement agencies in terms of digital forensics (Sridhar, et al., 2013). There are many definitions for the term of anti-forensics. This is due to lack of a consensus in defining what anti-forensics entails. (Joshi & Bhilare, 2014) States that AF is a set of techniques used as a countermeasure to forensic analysis.The growing menace of anti-forensics techniques and method have posed a great challenge to investigators and researchers. Based on their research work, (Joshi & Bhilare, 2014) stressed that the major purpose of AF is tamper with digital evidence at a crime scene. This negatively affects the output of the evidence, thereby decreasing the integrity and quality. (Rogers, 2006) posits the definition of anti-forensics as the act or attempt of compromising the usefulness and availability of a digital evidence during a forensic process . (Sartin, 2006) States that the ever increasing use and availability of sophisticated anti-forensics tools and techniques are a growing challenge for examiners not only in the law enforcement field but also in the public and private sector. The use of anti-forensics tools and techniques have become of great interest by both the government, private sector, criminals e.t.c, and it’s use on the increase to conceal and destroy data (Christian, et al., 2014) .An example of such growth in the use of AF tools is cyber criminals covering up their trails or company employees trying to commit fraud and avoid detection when carrying out a crime and also during a digital investigation. (Caloyannides, 2009) states that the use of digital forensics techniques and tools present a minimal effect on anti-forensic techniques. This is because most computer savvy can easily and readily defeat present forensics techniques and tools used. This is also stated by (Joshi & Bhilare, 2014) as most forensic techniques and tools cannot counter the effect of anti-forensics used by sophisticated individuals or organisations such as intelligence agencies and criminal networks. Present day forensic techniques can only apprehend naïve criminals who do not know how to cover their tracks or do not possess the technical knowledge of such tools. The concept of anti-forensics is not new, hackers make use of these techniques in compromising computer systems, bypassing intrusion detection tools and hiding malicious programs from anti-virus systems (Mohammad, et al., 2013)
(Harris, 2006) States the fact that the issue of anti-forensics is because there is no general standardization or framework in handling tackling the problem. This is of major concern as most analysts and researcher give different views on the issue of AF and also on the definition and what it entails.
Within the past few years, there have been a rise in the growth of anti-forensics that targets digital forensic tools. (Garfinkel, 2007) States that the rise of anti-forensics tools is due to the growth and dependability in the use of digital forensic tools in computer related and mobile crimes by examiners and digital investigators. It makes use of attacks on the investgator, and take advantages on the dependency of forensic tools and processes (Grugq, 2005) (Forster & Liu, 2005). An example is the metasploit framework, which makes use of different anti-forensic techniques and tools to bypass detection and evade forensic tools. This motion is backed up by (Hilley, 2007) stating that the use of frameworks like metasploit consists of anti-forensic asernals to pick on loopholes in digital forensic programs.
(Forster & Liu, 2005) and (Harris, 2006) described the major goals of anti-forensics. To avoid detection that any form of event occurred or took place, to distrupt the collection of vital information, to increase the time spent or needed on a case and casting doubt on the forensic report. (Harris, 2006) also pointed some more goals of anti-forensics. Forcing the forensic software to it’s presence, subverting the forensic software to turn against the organisation in which it’s running, launching a direct attack against the forensic examiner and leaving no evidence or presence of the anti-forensic tool.
2.6.2. Android Anti-forensics
As cited by most researcher, anti-forensic poses a greater threat to the forensic community. The threat of anti-forensics mobile devices have been ever increasing in use especially due to the presence of various free anti-forensic tools available on the web today (Caloyannides (2009), Garfinkel (2007), Mohammad, et al.(2013)). As stated by liu, et al.(2011) most forensic tools and techniques today do not keep up with the growth and progress in the field of anti-forensics. Most digital forensic tools available have become targets to forensic techniques and tools. The use of anti-forensic tools and techniques on android operating system is relatively new and increasing, various works have been done in the field of anti-forensics relating to android operating system and devices.
Distefano, et al. (2010)’s work “android anti-forensics through a local paradigm”discussed the concept of anti-forensic techniques and the effects on mobile device forensics. In this research work, the author focused on the concept of anti-forensic in android mobile devices and instantiated the need for related studies in the field of AF in android. The authors designed and implemented an AFDroid antiforensic application to evaluate the strengths of AF against forensic tools. The author’s research work proved that the use of anti-forensic techniques can deter forensic tools and produce false information in a forensic investigation.
Albano, et al. (2011) proposed a novel anti-forensic technique for the android operating system. The author proposed a technique to modify, erase and selectively delete digital evidence securely in an android device without causing much modification to the file system of the android OS. The author’s emphasized the possibility of modifying android operating system without using any cryptographic additions or low level modification of the android kernel.
Smith (2011) proposed an anti-framework for the android operating system called the Gumshoe anti-forensic toolkit. In the author’s research work, the concept of anti-forensic was outlined. The author emphasized on the possibility of exploiting the security mechanism of the android operating system and implemented a tool which alters digital evidence and manipulate the evident data in android operating system. For this project, this tool will be used to carry out simple anti-forensic manipulation and data hiding experiments. This will be used to evaluate the performance of the selected forensic tools against anti-forensics.
Sporea, et al.(2012) stressed on the issue of the readily available anti-forensic tools for smartphones. According to the author due to the relatively new field of anti-forensics, less research work have been done to address the issue of the use of these techniques in smartphone devices and stressed for the need of incorporation with the digital forenic techniques. The author’s made use two open source anti-forensic softwares and evaluated the performance of two leading forensic softwares against the forensic technique used. The results proved most forensic softwares do not fare well against open source anti-forensic toolkits.
(Karlsson, 2012) thesis work presented the issue of breach of trust in between forensic softwares and android operating system. According to the author, forensic tools place trust on the operating system when extracting digital evidence. Most forensic tools when carrying out logical extraction communicate and depend on the operating system to extract information. the author demonstrated the possibility of maniplating the android operating system to full the forensic toolkit to parse wrong evidence.
(Windram, et al., 2011) Emphasized the issue of lack of forensic tool testing against anti-forensic techniques. As stated by the author, most standard tools testing specification fail to incorporate the testing of forensic tools against the threat of anti-forensics. This creates a huge task for forensic investigator. The author’s experimented the possibility of manipulating forensic software’s.
In conclusion, there is the need of evaluation of forensic tools against the threat of anti-forensic techniques. As highlighted by the research community, the trend in the use of anti-forensic mechanism and techniques have been on the increase and most available forensic softwares do not keep up with the trend. According to some researchers, most forensic tools are not keeping up with anti-forensic techniques.
2.7. Performance Evaluation of Android Forensic Tools
As of writing, few research work has been done in terms of performance evaluation of android forensic tools. Works done were mainly focused on a particular section of forensic tools evaluation such as extraction capabilities of different forensic tools. Also, research works done were based on mainly desktop systems.
(Kovacik & Day, 2010) proposed a methodology for law enforcement investigators in carrying out victimm android phone analysis. In their research work, the authors carried out a comparison of top forensic tools and open source tools available. Two of these tools name were not given but the third tool was AFlogical, a tool also selected for this thesis. The author carried out a performance evaluation of three tools based on extraction capabilities of these tools. The results showed that the open-source tool Aflogical outperformed the two other commercial forensic softwares in extracting critical evidence. The authors stressed the need of a logical approach in terms of data acquisition in the absence of other forensic methods and SD cards.
(liu, et al., 2011) stressed on the issues facing the forensic community in relation to forensic tools. In their research work, the authors made emphasis on the issues of reliability, validity and effectiveness of forensic tools used in carrying out mobile forensics. The research work was focused on the reliability of forensic softwares used by investigators. They made use of the NIST methodology on evaluation of tools and also focused the anti-forensic approach. In evaluating the forensic tools, the use of an anti-forensic software was utilized in evaluating the performance of these tools. The results showed most forensic tools lacked the ability to detect the presence and alteration of evidence by anti-forensic tools and techniques.
(Kubi, et al., 2011) emphasized on the growing numbers of commercial and open source forensic tools used in mobile forensic. The authors pointed the growing challenges faced by investigators when selecting tools and also the problem of admissibility of evidence from forensic tools. The authors evaluated the performance of two leading forensic tools namely UFED Physical Pro 1.1.3.8 and mircosystem’s XRY 5.0 forensic software on two mobile devices namely the Sony Xperia XI and Nokia express music 5800. The authors evaluated the performance of both tools based on the NIST “Smartphone tool Specifications Standards” on core tool’s evaluation technique guidelines and using Daubert’s principle as a reference point towards digital evidence admissibility. The evaluation analysis was based on the reliability of the two tools and their admissibility in a legal settings. In the evaluation of the tools result, the use of graphical representation was used to compare the performance of both commercal tools. The result of the comparison showed microsystem XRY 5.0 outperformed the UFED physical pro 1.1.3.8 in terms of reliability.
(Knight, 2010) carried out an evaluation of software based tools used in the extraction of evidence in Iphone devices. Based on the authors research, the author stressed the challenges in retrieving evidence from iphone devices. The author emphasized the need of jailbreaking (rooting in android) of iphone devices in other to obtain more critical evidence. In the research work, the author compared two forensic softwares namely oxygen forensic toolkit and device seizure. In evaluation, the author compared both tools on the extraction result and carried out a comparison on the result output. The author concluded that the oxygen forensic suite outperformed the device seizure software in terms of extraction of evidence.
(Vijayan, 2012) carried out an evaluation of android forensic tools extraction capabilities. In the author’s research thesis, a comparison of three digital forensic tools were made based namely AFlogical tool, Oxygen forensic suite and mobil edit forensic toolkit and manual method of extraction. The author made an evaluation based on the overall output in terms of evidence extraction of all three tools and carried out a comparative analysis using the evidence extracted based on the reliability of evidence. The author concluded that the tools performed as expeccted based on the approached taken by the author.
(Shahzad, et al., 2013) Evaluated the performance of mobile forensic tools based on quantitative analysis. In their research, the evaluation of mobile forensic tool was done using a quantitative approach to measure the error of margin and the confidence interval (CI). In the author’s research work, an evaluation of two tools namely UFED physical pro 1.1.3.8 and XRY 5.0 was done. In evaluating the performance of these tools, the author carried out tests on the tools based on the success rate in extraction and the margin of error in which these tools exhibited. In their conclusion, the XRY forensic tool had a higher success rate and a little margin of error than UFED physical forensic suite.
In summary, most research works have based the evaluation of android forensic tools based on the issue of integrity and reliability of evidence. Major evaluation methods used all based their evaluation methodology on the amount and ratio of correctness of digital evidence extracted from forensic tools.
2.8. Summary and Conclusion
This section gives a conclusion of the literature review chapter. The literature review outlined the definition and the essence of digital forensics. In the literature review the concept of mobile forensics was stated in the first section. As cited by researchers, the mobile forensics poses more challenges to digital examiners and investigators than computer based forensic investigation. As reviewed in the literature review, mobile forensic tends to be daunting and difficulty compared to the computer based forensic aspect. As stated in the review, the issues faced with mobile forensics can be classified into two major categories of problem namely technical and legal challenges. In other to carry out mobile forensics, the essence of mobile forensic investigation process model has been outlined in the literature. For a forensically sound digital investigation, an investigator must be able to follow certain guidelines to ensure admissibility and integrity of digital evidence. For better understanding of performance evaluation of android forensics tool, a review of android forensic tools and android operating system was carried out to know how android and how android works and the various component of android architecture and what tools exist in carrying out android forensics. As stated above, android consist of 5 core layers. A review of past works was done on android forensics. From findings, various methodology exists in carrying out android forensics. As highlighted by some in the research community, some methods are arguably not forensically sound and some preserve the integrity of evidence extracted from android devices.
The issue of anti-forensics was discussed in this chapter. As emphasized above, there is a growing rate and increase in the use and availability of anti-forensic software in digital forensics as a whole. As discussed in the anti-forensic section, the threat of anti-forensic poses a great challenge to digital forensic tools and android operating system. A detailed review of past works was done anti-forensic in android.
The last section of chapter two gave a detailed review of literature of pasts work done in performance evaluation of android forensic tools to give a better understanding of the various methods employed by researchers in past work in evaluating forensic tools. Various research work based their emphasis on the performance of tools based on reliability of extraction output.
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more