Penetration Testing Vs. Ethical Hacking
Contents
Penetration Testing & Ethical Hacking
This document will discuss the differences between penetration testing and ethical hacking. It will then continue to discuss the requirements in a corporate environment and the legal issues that can occur while performing an ethical hacking engagement.
Hacking is a term used to cover all methods of attacking a computer system. Ethical hacking is the process of testing and attacking systems with the permission of the systems owner while staying within the bounds of the law (Wilhelm, 2013, p12). Penetration testing is a structured methodology for identifying vulnerabilities in a network. There are several phases which include an information gathering exercise, scanning and mapping a network, identifying systems, and finally checking for open vulnerabilities (Wilhelm, 2013, p78). Much of the material about ethical hacking and penetration testing does not differentiate between them (Regalado et al., 2015). “Despite that these two terms are often used interchangeably; there is a thin but distinct enough line between them.” (Kostadinov, 2016). The penetration testing methodology can be implemented by anyone and falls under the broad banner of hacking (Regalado et al., 2015). There are several other skills and processes included in hacking such as cracking, source code analysis, fuzzing, zero-day research and malware writing (Regalado et al., 2015).
Penetration testing is used by both ethical malicious hackers and has no requirement for it to be ethical or with permission (Wilhelm, 2013). An ethical hacker is known as a White Hat and their counterpart is the Black Hat (Hoffman, 2013), ethical hackers must report their findings to the client but a malicious hacker might exploit any vulnerabilities identified for gain. While the boundaries of a contract and the laws of the land can hinder a White Hat, a Black Hat has no such boundaries (Regalado et al., 2015). This means that the ethical hacker can never 100% test a system in the way a malicious one can.
When engaging in a penetration test, an ethical hacker follows set processes including definition of the engagement, discovery of information and the environment, exploitation of vulnerabilities and reporting to the client (Figure 1).
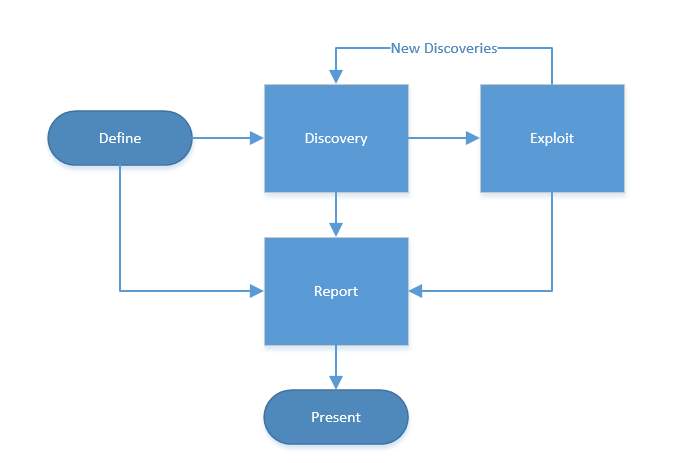
Figure 1: The penetration testing methodology (United States, Department of Commerce, 2008)
In the definition stage, an ethical hacker will agree the scope of the project, stakeholders, targets and boundaries the company wishes to enforce. This information should form the basis of a contract between the two parties and is an important step in making sure the hacker remains ethical (Wilhelm, 2013).
The discovery phase is a two-step process and is where the penetration test begins (United States, Department of Commerce, 2008). Both White and Black hats start their process of discovery with reconnaissance, which can be further broken into two categories: passive and active (Wilhelm, 2013). Passive reconnaissance can be as simple as using a search engine or the company’s website to investigate attack avenues or it can mean some social engineering of employees (Gregg, 2006). Web tools such as http://www.netcraft.com allow a hacker to gather information about the external web sites of the target (Figure 2).
Active reconnaissance normally involves trying to scan and identify the network topology which gives the hacker an idea of the security measures in place, IP ranges and interactions between systems (Gregg, 2006). A hacker typically needs to learn as much about the target as possible before engaging in the rest of the process. Tools such as dig can be used to interrogate the DNS servers of the target enumerating the hosts and services in use (Figure 3 & Figure 4). A hacker could then use the information from DNS to connect to common services using a tool like netcat (Figure 5).
After a hacker has gathered information about the target, the scanning phase begins which looks for weaknesses in the environment. This can be done independently of a penetration test as a vulnerability assessment (United States, Department of Commerce, 2008). The hacker then attempts to identify active hosts and open ports. One method is to perform a ping sweep using tools such as Nmap (Figure 6). The hacker can also achieve this passively if they are directly connected to the target network by monitoring ARP traffic on a network segment using a tool such as netdiscover (Figure 7). It is important to verify gathered data and where possible, the ethical hacker should use multiple tools to cross-reference the information (Wilhelm, 2013, p181). With this information, the hacker can build up a good picture of what the network looks like and identify vulnerabilities in the discovered devices.
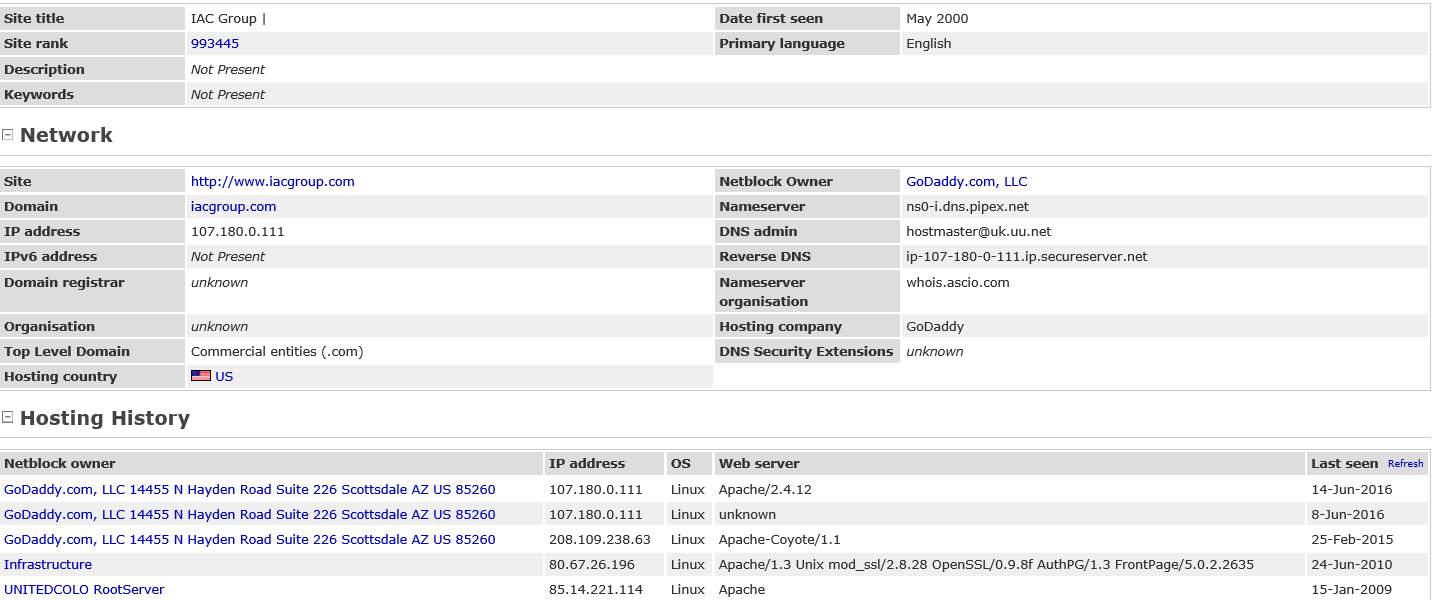
Figure 2: Report of the current and historical information netcraft gathered about a website
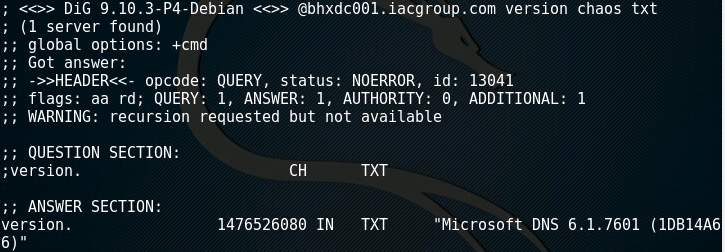
Figure 3: Output of dig after querying a DNS server for its version.
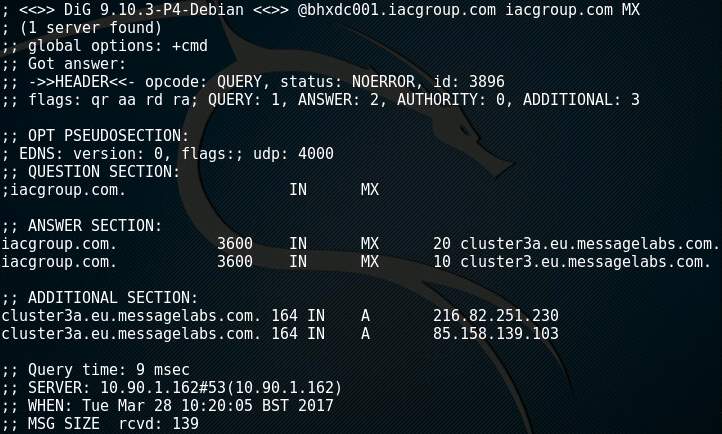
Figure 4: Output of dig after querying a DNS server for MX records.
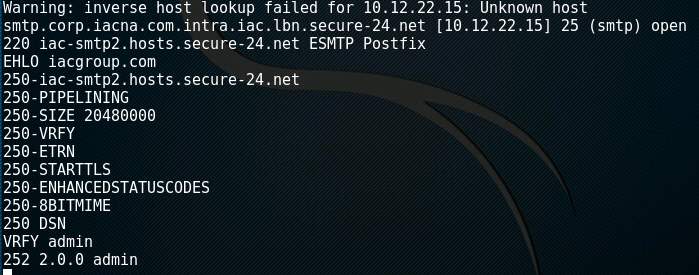
Figure 5: Output of netcat querying an SMTP server using the VRFY command.
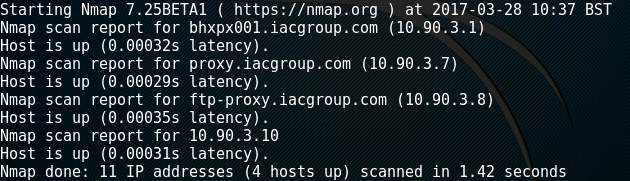
Figure 6: Output of Nmap performing a ping sweep of a network segment.
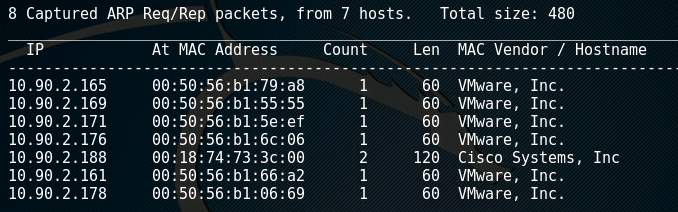
Figure 7: Output of netdiscover monitoring a network segment for ARP packets.
At the exploitation stage, the attacker knows what is available on the target network such as what systems exist and what services are available to exploit. They can then attempt to gain access. One way system identification can be achieved is by using Nmap with the O option (Figure 8). The attacker can achieve this passively by monitoring ARP traffic on a network segment using a tool such as p0f (Figure 9). Another option to identify a specific service from an open port is to use a method called banner grabbing (Wilhelm, 2013). Nmap can achieve this using the sV option (Figure 10). The hacker can use this information to search websites such as https://www.exploit-db.com to find exploit source code.
An ethical hacker can be restricted by the terms of the engagement or legal jurisdiction (Wilhelm, 2013). Additionally, leveraging vulnerabilities may cause a system to crash or cause data loss (Wilhelm, 2013). A company will likely stipulate that any attempts to gain access must be non-destructive, which could hinder an ethical hacker’s ability to assess the company’s network fully. Every action during the engagement must be documented in detail and remediation activities included for each of the exploits identified (Regalado et al., 2015).
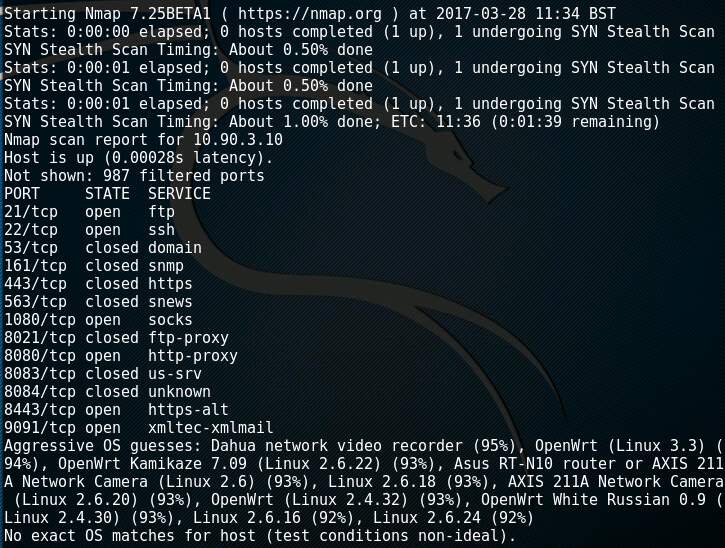
Figure 8: Output of Nmap attempting OS Identification of a host.
(Note: The detection did not work)
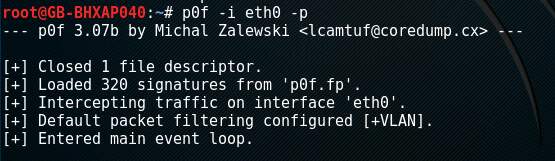
Figure 9: Screenshot of p0f monitoring a network segment for hosts.
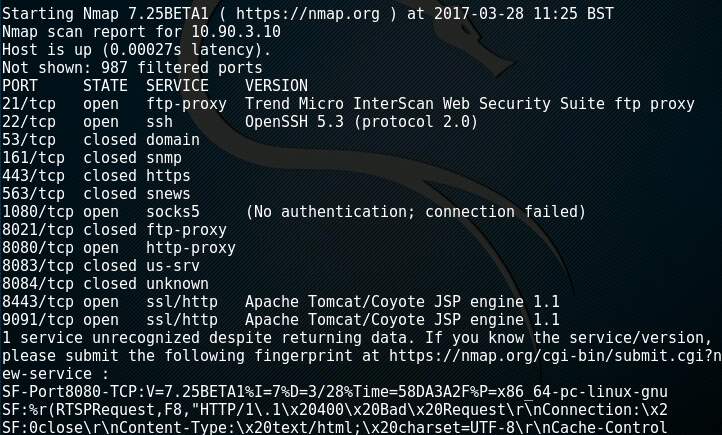
Figure 10: Output of Nmap attempting service identification using banner grabbing.
(Note: The system from figure 8 identifies itself on port 21/tcp)
Ethical hackers walk a line between fully testing the security of a network and the laws that govern the country where they are operating. For example, in the discovery phase a hacker could use social engineering but the data gathered from this exercise may violate data protection laws such as U.S. Privacy Act 1978 or U.K The Data Protection act 1998 (Regalado et al., 2015,Wilhelm, 2013).
Business inter-connects are high risk as there is an implicit trust yet the engaged company has no control over the security of 3rd party networks. Leveraging these connections would be illegal if the 3rd party has not given consent and the ethical hacker would break laws such as U.S. Computer Fraud and Abuse Act 1986 (Amended 1996) or U.K The Computer Misuse Act 1990.
The ethical hacker leaves themselves open to prosecution if they do not have a clear contract outlining all the acceptable actions for the engagement (Regalado et al., 2015,Wilhelm, 2013). “To complicate matters, the laws of one country are not compatible with the laws of another country, and in some cases, they even contradict each other” (Wilhelm, 2013). This requires the ethical hacker to work within the boundaries of multiple legal frameworks. Additional considerations are needed to move data across physical borders as some countries have laws controlling where information can be located (EU Safe Harbour Directive).
Ethical hacking is required to assess the risk to an organisations network. “To protect themselves, organisations may want to understand the impact and ability of an attacker” (Regalado et al., 2015). Since organisations know t malicious hackers can attack their network, ethical hacking allows them to emulate the role of those potential attackers and then outputs the data (Regalado et al., 2015). The organisation can use the identified risks and recommendations to address threats before they are exploited.
The traditional idea of putting in a perimeter firewall, using policies such as least privileged access and change management are not enough to keep a network safe from incursion. There are many reasons a malicious person may wish to probe and attack a network. It could be for monetary gain, industrial espionage, kudos, political motivations or “for the Lulz” (Lulzsec: UK Men Plead Guilty to Hacking Charges. 2012, Pfleeger, Pfleeger, & Margulies, 2015).
Having an assessment done by an ethical hacker will increase the security of a company network but it will never make it 100% secure (Wilhelm, 2013). This is largely because a corporate network is a moving target and every time a change happens, it can introduce a threat that previously did not exist. Therefore, it is critical that a company continue testing on a regular basis to reduce their attack vectors.
References
Lulzsec: UK Men Plead Guilty to Hacking Charges. (2012) [Online] Available from: http://www.bbc.co.uk/news/technology-18577609 [Accessed: 29/04/2017].
Gregg, M. (2006) The Seven-Step Information Gathering Process. [Online] Available from: http://www.pearsonitcertification.com/articles/article.aspx?p=472323&seqNum=5 [Accessed: 25/03/2017].
Hoffman, C. (2013) Hacker Hat Colors Explained: Black Hats, White Hats, and Gray Hats. [Online] Available from: https://www.howtogeek.com/157460/hacker-hat-colors-explained-black-hats-white-hats-and-gray-hats/ [Accessed: 15/03/2017].
Pfleeger, C. P., Pfleeger, S. L. & Margulies, J. (2015) Security in Computing. 5th edn. Westford Massachusetts: Prentice Hall. pp. 54-56.
Regalado, D. et al. (2015) Gray Hat Hacking: The Ethical Hacker’s Handbook. [Online] 4th edn. McGraw Hill. Available from: https://www.amazon.co.uk/Hacking-Ethical-Hackers-Handbook-Fourth-ebook/dp/B00QSEJNIM/ref=tmm_kin_swatch_0?_encoding=UTF8&qid=&sr= [Accessed: 22/01/2017]. pp. Chapter 1.
United States. Department of Commerce. (2008) Technical Guide to Information Security Testing and Assessment. Gaithersburg Maryland: National Institute of Standards and Technology. (SP-800-115).
Wilhelm, T. (2013) Professional Penetration Testing. 2nd edn. Massachusetts USA: Syngress. pp. 12-13, 16, 22-35, 78, 152, 233.
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more