Abstract:
This paper report looks more into the advancement towards the Information security systems. This report shows the importance and the changes that an organization could accomplish by strengthening the IT security system. We contend that there are a helpful task the executive’s approaches that influence the security system associated with most of the condition in an organization. In some situation, though replicating upon field-responsibility, the share of these technology security methods perform to just not work in the world exemplified through undertaking help and crisis help ventures. This brings up some intriguing issues, despite the fact that an organization has demonstrated its accomplishment in development strategy. There are issues related to the way in which the framework has been Chosen as well as actualized that have prompted security issues.
There are representative adoption diminishes the effectiveness of IT security investments in the likelihood of a breach. Contrary to the employment of a lot of IT security isn’t directly chargeable for reducing breaches, however instead, institutional factors produce the conditions below that IT security investments can be more effective. Implications of those findings area unit important for policy and observe, the foremost necessary of which can be the invention that companies ought to take into account however adoption is influenced by institutional factors and how this could be balanced with technological solutions (Angst, C. M., Block, E. S., D’Arcy, J., & Kelley, K., 2017). In particular, this report results support the notion that deeper integration of security into IT-related processes and routines ends up in fewer breaches, with the caveat that it takes time for these advantages to be completed.
Introduction
Technology and its critical factors that plays a major role in every organization. IT security is a set of security strategies that help an organization in preventing any kinds of unauthorized attackers on its asset and IT sector. IT security helps in blocking the access of sophisticated hackers my blocking their asses to this sensitive information. Depending upon the purpose and the kind of information, activity, there are different kinds of a security strategy that can be implemented or even developed as per the requirement. With the number of details and components that you just got to place along, it’ll be best for using strategic designing listing examples that ensure that explicit security issues, action plans, strategies, relevant data, and problems are going to be enclosed within the document.
More important, an organization platform for IT security enable cyber-security to develop the infrastructure for personals working on the products for information security, creating across the department and functional areas to ensure a strong but flexible security barrier. The result is faster planning and stronger enforcement of security policies. This creates an ability to achieve sustained compliance with organization and government standards on the security, a comprehensive, well-documented procedure and policies. And overall cost-effective and saves the company income by reducing unwanted expenses by reducing security attacks and its aftereffects.
This report will review some of the basic issues that relate to information security process, industrial threats and some the ways to prevent them. Including the challenges in enforcing security requirements that are involved in information security and compliances processes.
Importance of information security:
Every organization is built with a solid base of resources, it can be information they handle or it can be the people who work for the growth of the organization. In fact, respective of the resource it is important to protect them. the future of an organization depends on its assets. And protecting then should be the priority of an organization. Even though IT security and information security is commonly considered similar, they are two different types of security. The type of security that focuses to secure sensitive information and develop tool protect sensitive organizational information is referred to be information security, whereas IT security focuses more on securing digital data and network security from hackers and other malicious attacks.
Common threats to IT security
IT security faces threats of different forms. A common threat that is popular in the industry is malware, or malicious software, which may come in different variations to infect network devices, including:
• Ransomware
• Spyware
• Viruses
It is important to have reliable security and best practice awareness to stay protected. Learning more and trying to undertint any malicious activity is the first step to be prepared on these attacks.
Source: COMODO creating trust online
How IT security is beneficial?
IT security prevents malicious threats and potential security breaches that may have a large impact on your organization. When you enter your internal company network, IT security helps ensure only authorized users can access and make changes to sensitive information that resides there. IT security works to make sure the confidentiality of your organization’s information.
Few types of IT security
• Network security
Network security is employed to foresee unauthorized or malicious users from obtaining within your network. This ensures that usability, reliability, and integrity are uncompromised. This type of security is important to prevent a hacker from accessing information within the network. It conjointly prevents them from negatively poignant your users’ ability to access or use the network. Network security has become more and more difficult as businesses increase the number of endpoints and migrate services to the public cloud.
• Internet security
Internet security involves the protection of knowledge that’s sent and received in browsers, furthermore as network security involving web-based applications. These protections are designed to watch incoming network traffic for malware furthermore as unwanted traffic. This protection might are available in the shape of firewalls, antimalware, and antispyware.
• Endpoint security
Endpoint security provides protection at the device level. Devices that will be secured by endpoint security embody cell phones, tablets, laptops, and desktop computers. Endpoint security can forestall your devices from accessing malicious networks that will be a threat to your organization. Advanced malware protection and device management package are samples of endpoint security.
• Cloud security
As the technology advances Applications, data, and information area are moving to the cloud, which means users area unit connecting on to the web and don’t seem to be protected by the normal security stack. Cloud security will facilitate secure the usage of software-as-a-service (SaaS) applications and therefore the public cloud. and cloud-based unified threat management (UTM) will help in issues based on cloud security.
Importance of Security Strategic Plan for a Business
A well-designed marketing strategy the best way to take a product to a customer, similarly the planning a better strategy and action plans to secure business security is more crucial for its business. Security strategic plans can be developed by taking multiple points in mind including business information data, digital assets, and data, the location of the organization, internal personal security, and corporate relationships. Below are some of the reasons why it is important for any organization to have a strong security strategic plan.
1. A security strategic plan defines the condition of the security in which business needs to run. This provides a goal and objective that needs to be ensured any organization to maintain or improve its security level.
2. A security strategic plan helps in managing security risks. With the help of this plan, a well-documented security measure is developed. This will prepare a business to analyze the impact and results of any threats and risks on an attack. This is one of the best ways when it comes to business operations even if there are possible security issues that are necessary to be addressed at the moment or in the future.
3. A security strategic plan will help in gathering all the entities that are present in the business and practices together to develop an understanding regarding their responsibilities when it comes to preserving the safety and security of the corporate location. This document can also help define particular terms and instructions which can make the plan more comprehensible.
4. A security strategic plan will help in preparing an action plan and picking strategies that can promote the procedures for developing the security either in a specific business area or the entire workplace. This can help the organization to define its security restrictions and establish procedures where it would like to take the security policies and protocols of the industry.
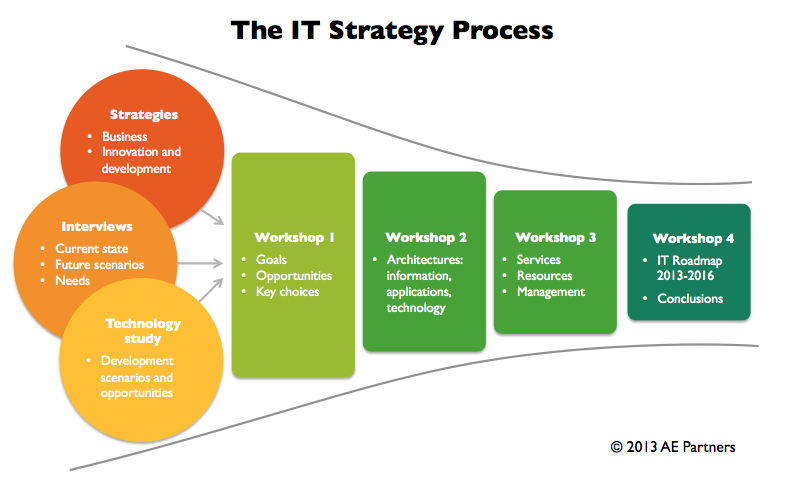
Source: IT SECURITY & STRATEGY
Human factor in IT security:
The human factor is a common factor in IT security, sometimes people may take cybersecurity necessities too casually, leading to theatrical significances for the organizations they work for.
Recently WannaCry ransomware epidemic, there is a major role played by the human factor in making organization worldwide helpless. Two months after the unveiled weaknesses had been patched with a new update from Microsoft, many businesses around the world still hadn’t updated their systems. Numerous cases non-IT workers are considered as the weakest link, this is because of these workforces with local administrator rights who disabled security solutions on their computers and unknowingly will spread the infection from their computer onto the entire company network.
Inside risk:
In contradiction of the environment of a complex and growing cyber threat background, where 57% of industries now assume their IT security will turn out to be compromised, businesses are also awakening up to the fact that one of the major chinks in their armor against internet threats is their own workforces. In fact, 52% of corporations admit that personnel is their biggest softness in IT security, with their insensitive actions pushing business IT security strategy at threat.
The terror of being put at risk from inside can be seen clearly in the fact that for industries, the top three cybersecurity fears are all related to human factors and member of staffs actions. The table below shows that industries are attentive of how easy it is for employee/human error to influence their corporation’s safekeeping. They concern most about workers sharing sensitive data via mobile devices (47%), the loss of mobile devices exposing their company to risk (46%) and the use of inappropriate IT assets through personnel (44%).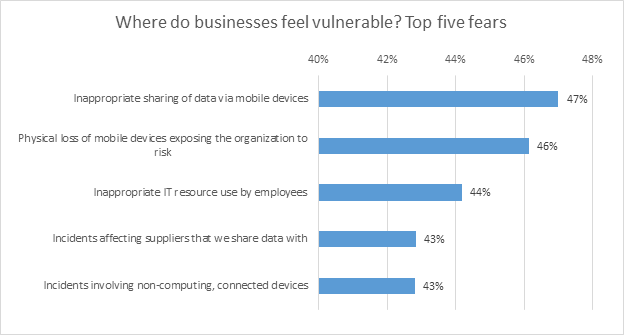
source: IT Security Risks Survey 2017, global data
Best Practices in IT security:
It the ultimate goal of an organization to more secure. Most of the security workforce agrees that not a matter what they do to secure the security there is always something causing a breach in the system.
Even though security crews have been fighting a situation of constantly changing external attacks for years, now they are also responsible for addressing the risk of insider breaches. The reality is, the majority of administrations will face some sort of breach, whether it comes from external or insider threats.
To make sure you’re equipped, it is important to take a step by step approach with your establishment’s security. Below are a few cybersecurity best practices that can be considered for increasing the IT security
Listing a few Cybersecurity Best Practices
It is important to take step by step approach within an organization’s security. These cybersecurity best practices may be considered
1. Follow proper IS Governance Method
Creating and preserving an information security outline is a great place to start. This outline is more important than every glossy tool in your security stack, as it should align your guarantee strategies and backing the industry.
When choosing one of these approaches, confirm your program provides the capability to engage a risk-based method and enables your groups to sense events, inspect successfully, and react quickly.
2. End Data Loss
Most businesses rely on a member of staff trust, but that won’t stop losing data from the company. A recent study of more than 1,500 security professionals uncovered that data exfiltration from an endpoint is the top security worry of 43% of them. Now, more than ever, it is enormously imperative to control access, overseer vendors and services as well as employees, and know what your consumers are doing with business data to reduce data leakage.
3. Identify Insider Risk
It’s really that employees are your major assets, but it is also true that they can also be the biggest risk. Although well-trained workers can be your security front line, you still want technology as your last line of protection. Observing user activity allows you to detect unlawful performance and verify user actions are not violating security policy. Insider threats may go unnoticed, but the fact of the matter is insider breaches are awfully expensive.
4. Backing Up information
Backing up files may appear like common sense, but any business that has been affected with ransomware like Petya or Wannacry is a perfect example for telling how important it is to safeguard this best practice. It is crucial for the corporation to have a full working back up of all of the data not only for a routine security purpose but also for any potential rising attacks.
5. Mitigate Social Engineering
The technology and IT security policies implementation doesn’t substitute the need for common sense or remove human error. Social engineering strategies have been used effectively for decades by acquiring login information and contact with encrypted files. Efforts may come from emails, messages or other means of communications. The best defense is to create awareness for the working group.
6. Educate and create awareness to users
No matter how smart the people are, still they are the weakest link when it comes to information security. But this do not mean the threats cannot be avoided by the risk through frequently educating the users on cybersecurity best practices. All the training programs should include how to identify a phishing email, generate and sustain strong passwords, avoid unsafe applications, ensure treasured information is not taken out of the establishment.
In these programs could feel like unvalued waste of work hours but in long run it will crate an impact to the users to follow the practices they learn. Finding resourceful techniques to make the training more entertaining will help more in making the program successful.
7. Plan usage policies for New Personnel and 3rd Parties
To reinforce and simplify the education for cybersecurity best practices you give your users, you should clearly framework the necessities and expectations your company has in regards to IT security when you first hire them. It is recommended to make sure employment contracts clearly describe these security requirements.
8. Create an Incident Response Playbook
No matter even if the best practices is well followed, there always a change it could fail. In fact, nearly most of the organizations suffers a security incident at least once an year. In case of such incident having a response, plan laid prepared a head of time will help to close any vulnerabilities and help in limiting the damage of a breach.
9. Update Software and Systems
The simplest and sometimes the most effective way to protect against any attack is my making sure the all the software and application is UpToDate. Enabling auto update feature will help the software to update itself to the latest level, this will improve the protection of the software to fight against any potential attach in the industry.
10. Uphold Compliance
Optimistically these best practices are a useful policy for keeping a business safe, but you do have another set of guidelines available to you. Guidelines like HIPAA, PCI DSS and ISO provides benchmarks for how a business should manage its security. More than a stress, which you need to prepare audit logs for, guidelines can help guiding a business to a more secure future.
Conclusion:
A 100% security is not guaranteed by any method but securing the data of an organization a crucial part of its future. IT is a broad area and covering the entire sector is like impossible. But if we follow necessary actions, a secure system can be developed which can support an organization. Following the best practices along with proper security guidelines will strengthen the security of an organization. Investing in developing IT security is certainly and best decision of the business.
References:
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more